 |
Chen Zhi. Photo: Prince Holding Group . |
The cryptocurrency community received shocking news when the US Department of Justice indicted Chen Zhi, Chairman of Prince Holding Group (headquartered in Cambodia), on charges of running a global online fraud ring, money laundering, and using forced labor.
The notable detail in the case comes from the amount of cryptocurrency seized, which includes 127,271 BTC, currently worth about $15 billion . This is the largest amount of Bitcoin ever seized by prosecutors.
“This is the largest virtual asset seizure in history,” the US Justice Department stressed in an official statement. The money is believed to have come from fraudulent activities such as “pig slaughter,” then laundered through a complex network of legitimate businesses, shell companies, and large-scale Bitcoin mining operations.
Suspicious signs
According to the US Department of Justice records, Chen holds multiple nationalities including China, Cambodia, Cyprus, Vanuatu... and holds the position of Chairman of Prince Group. On the surface, this is a real estate, financial services and consumer group. However, the most profitable activities come from fraudulent complexes using forced labor in Cambodia.
Most of the scams come from the form of “pig butchering”. In this, scammers build fake relationships on the Internet, create trust and then lure victims to invest in fake exchanges and wallet platforms.
The document accuses Chen of directly managing the scam establishments, holding records that clearly mention the form of “pig slaughter”. This person even kept a notebook recording the scam scenario, targeting victims in many countries such as Vietnam, Russia, China, Europe...
In 2018, the Prince Group’s illegal and “pig-slaughtering” scams brought in about $30 million a day, laundered through a complex network to conceal its origins.
 |
Prosecutors said Chen Zhi kept photos illustrating Prince Group's "brute force methods" to train employees to commit fraud (pictured above). Photo: U.S. Attorney's Office Court Records . |
According to the records, the illegal profits were used to fund large-scale cryptocurrency mining operations, involving several companies such as Warp Data Technology (based in Laos) and Lubian (based in China).
“For a time, Lubian had the sixth largest Bitcoin mining operation in the world . Chen once said that the profits were huge due to low costs, meaning that the operating capital of these businesses came from money defrauded from Prince Group victims,” the document stated.
Between November 2022 and March 2023, Warp Data received more than $60 million from Hing Seng, the shell company used to make payments, including to Awesome Global's directors and their spouses, and to purchase multimillion-dollar luxury items such as Rolex watches and Picasso paintings.
Chen and his co-conspirators also combined their ill-gotten gains with newly mined Bitcoins to obscure their origins. For example, Lubian’s addresses received large sums of money from sources unrelated to mining, with the proportion of new Bitcoins in Lubian’s wallets being only about 30%.
Sophisticated action
Most of the newly mined Bitcoins were transferred to a non-custodial wallet (held by Chen), which also received non-mining funds from the cryptocurrency exchange platform Exchange-2.
In the case, Exchange-2 was the centralized exchange used by Chen and his co-conspirators to transfer cryptocurrency. The money laundering activities involved transferring funds from Exchange-2, splitting them across multiple wallets, and then pooling them and mixing them with newly mined Bitcoins.
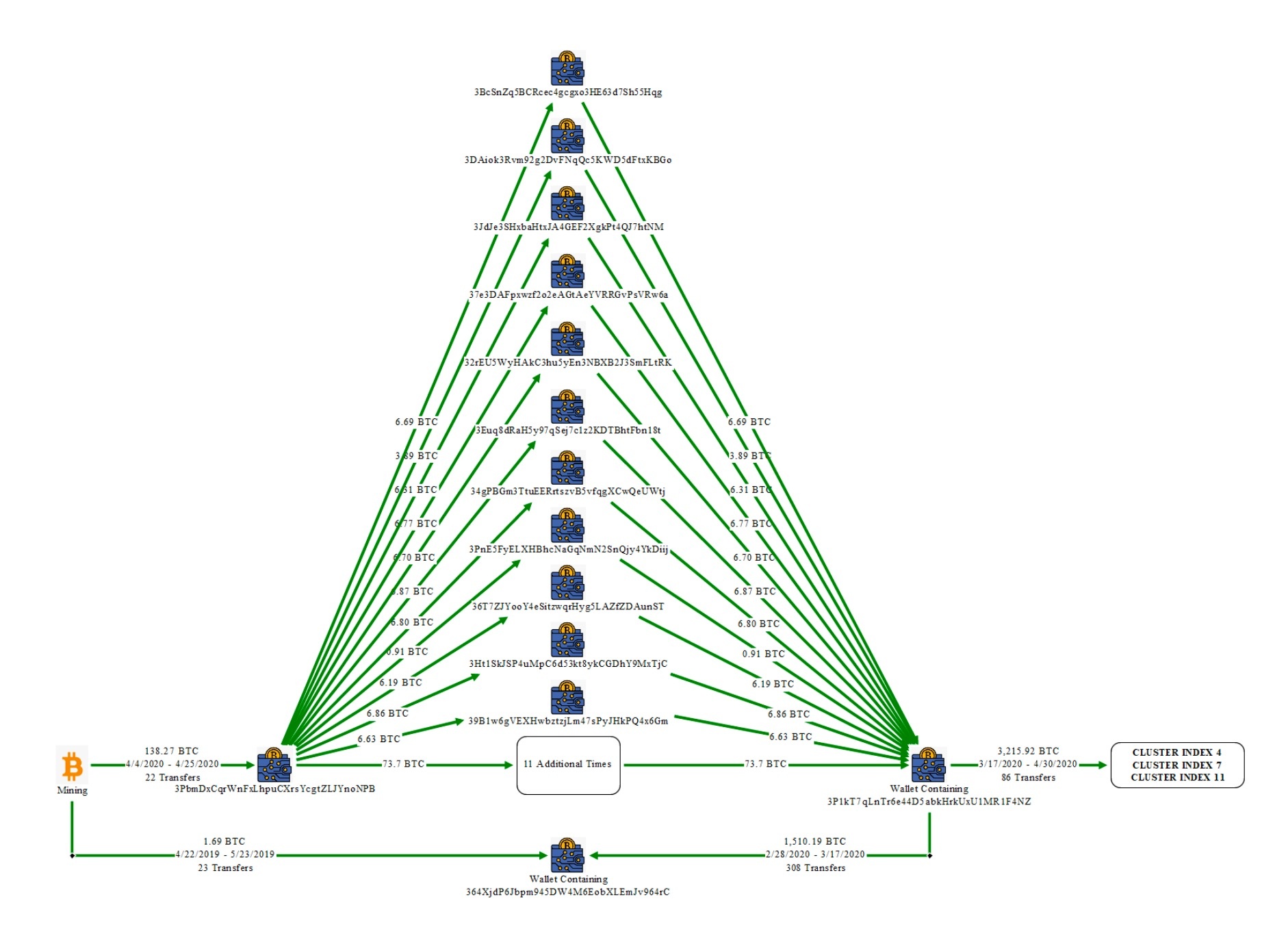 |
The diagram shows money from the bitcoin mining pool was divided into 22 wallet addresses, consolidated into other addresses and then transferred to Chen's personal wallets. Photo: US Department of Justice . |
Chen and his associates used multiple layers of money laundering techniques to conceal their origins. Shell companies were set up such as FTI, Amber Hill Ventures, LBG, and opened bank accounts in the US by deceiving business activities and sources of income.
The ill-gotten funds were moved through centralized exchanges, such as Exchange-1 and Exchange-2. Exchange-1, based in China, was described as “favored by foreign criminals” because it did not cooperate with the US government and hid transactions.
Based on the records, the cryptocurrency was divided into dozens, even hundreds of wallets. They were then pooled into several unhosted wallets held by Chen.
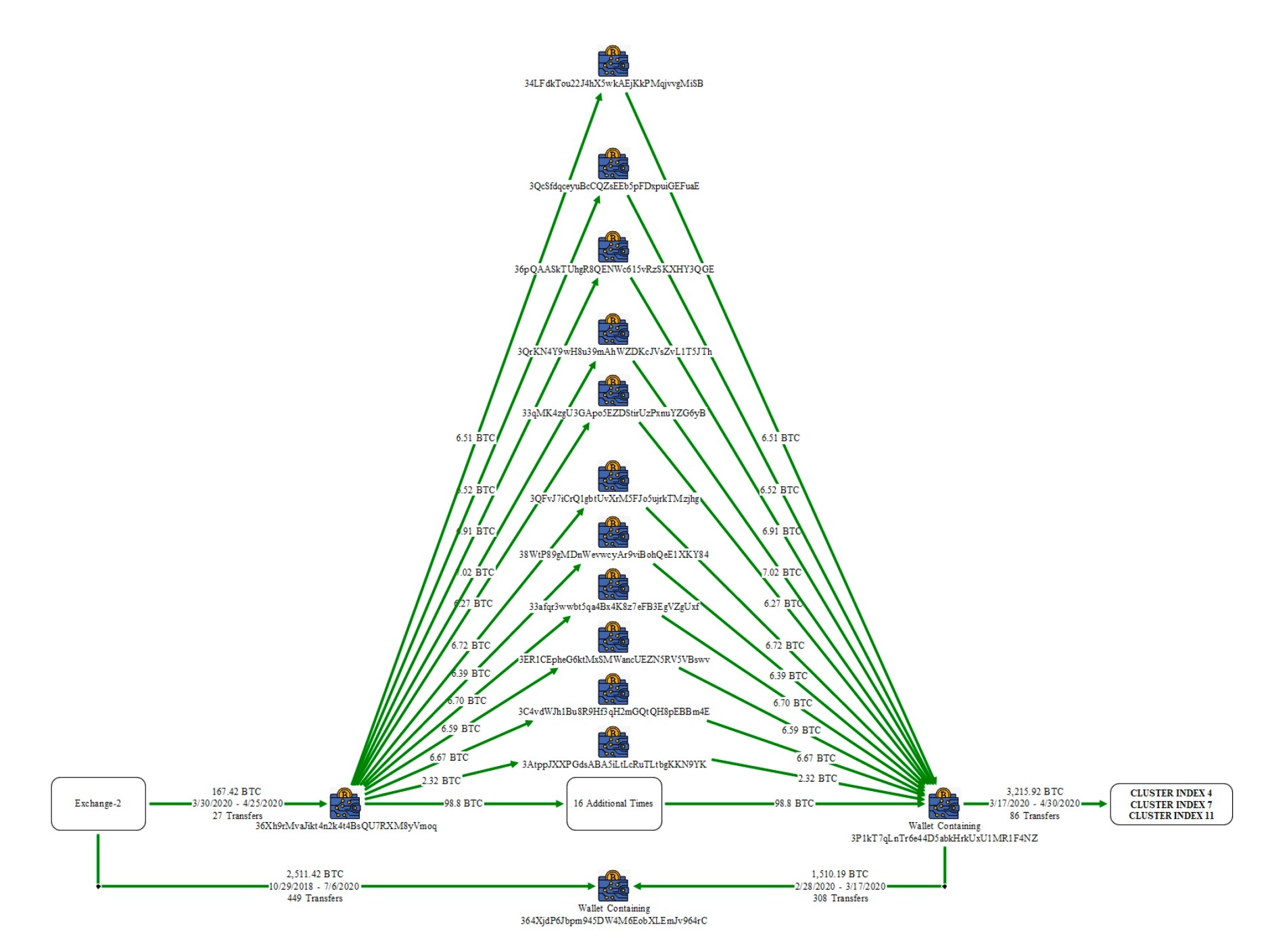 |
Money from Exchange-2 was also divided among 27 wallet addresses, combined into other wallets and then transferred to Chen's personal wallets. Photo: US Department of Justice . |
A diagram from the US Federal Bureau of Investigation (FBI) shows that money from a Bitcoin mining pool was divided into 22 different wallet addresses, then consolidated into one address and transferred to Chen's wallet.
Similarly, coins from Exchange-2 were split into 27 addresses and then merged into other addresses, forming a complex transaction pattern.
It is noteworthy that the transactions were sent in similar amounts and times. The similarities suggest that the bitcoins from Exchange-2 (the scam money) were intentionally transferred to mimic transactions from bitcoin mining pools, creating the illusion that all the money in the wallet came from regular mining operations, hiding the remaining source of illegal funds.
How the FBI Seizes Bitcoin
FBI officials stressed that the seized funds were not on the exchange, but stored in Chen's wallet.
To trace the funds, the agency identified the primary sources of funds for Chen’s 25 personal wallets. The funds primarily came from two sources: bitcoin mining operations (via Lubian and Warp Data), as well as indirect transfers from centralized exchange wallets to wallets controlled by shell companies.
FBI agents grouped the 25 addresses into 13 clusters (Cluster Index-1 to Cluster Index-13) based on similar transaction times and values. The process of splitting and pooling funds was modeled by the FBI as a network of custodial and non-custodial wallets, which the agency confirmed was a “clear indicator of money laundering activity.”
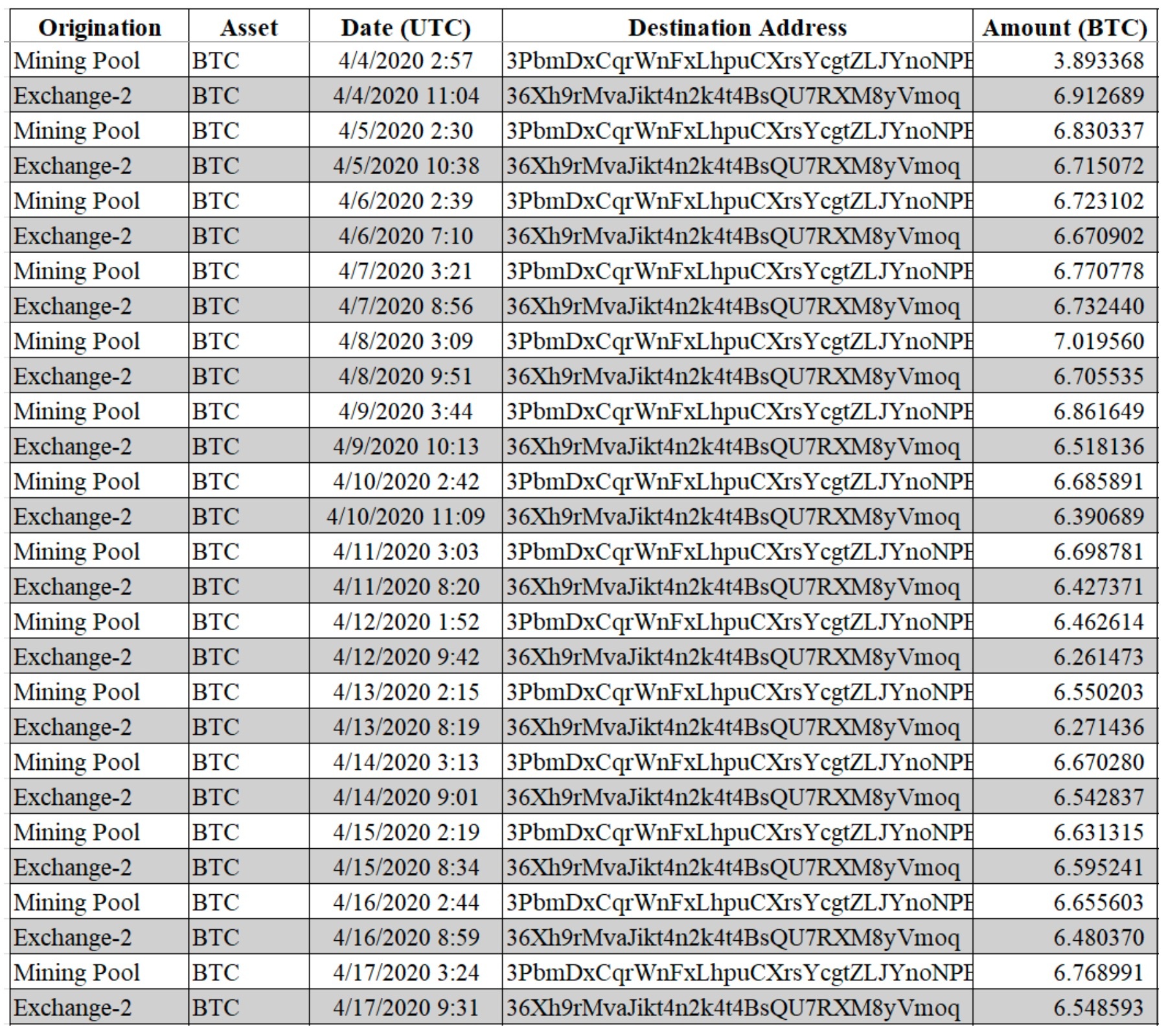 |
Time and value of transactions receiving money from bitcoin mining facilities and Exchange-2. Photo: US Department of Justice . |
The FBI demonstrated that half of the seized bitcoins (approximately 61,230 BTC) were transferred to Chen's personal wallet through three main transaction groups, including transactions from coin splitting/pooling techniques and coin mixing from mining and illicit profits.
Internal evidence also demonstrates money laundering activities by Chen and his co-conspirators, including documents that explicitly refer to “BTC washing.”
According to the filing, the seized bitcoins are no longer in Chen’s 25 personal wallets, but are now stored in addresses controlled by the US government. As for how the Bitcoins were seized, the document states that Chen “personally maintained the wallet addresses and seed phrases associated with the private keys of each wallet.”
Although it did not specify how, during the investigation and search, the FBI has the ability to physically seize storage devices such as computers, hard drives... or books of Chen related to Chen's private keys and seed phrases. With this data, the US government can transfer money to safe addresses.
Source: https://znews.vn/cach-my-thu-hoi-15-ty-usd-bitcoin-cua-tran-chi-post1594720.html


![[Photo] Collecting waste, sowing green seeds](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/18/1760786475497_ndo_br_1-jpg.webp)



![[Photo] General Secretary To Lam attends the 95th Anniversary of the Party Central Office's Traditional Day](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/18/1760784671836_a1-bnd-4476-1940-jpg.webp)
![[Photo] Closing ceremony of the 18th Congress of Hanoi Party Committee](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/17/1760704850107_ndo_br_1-jpg.webp)



























































































Comment (0)