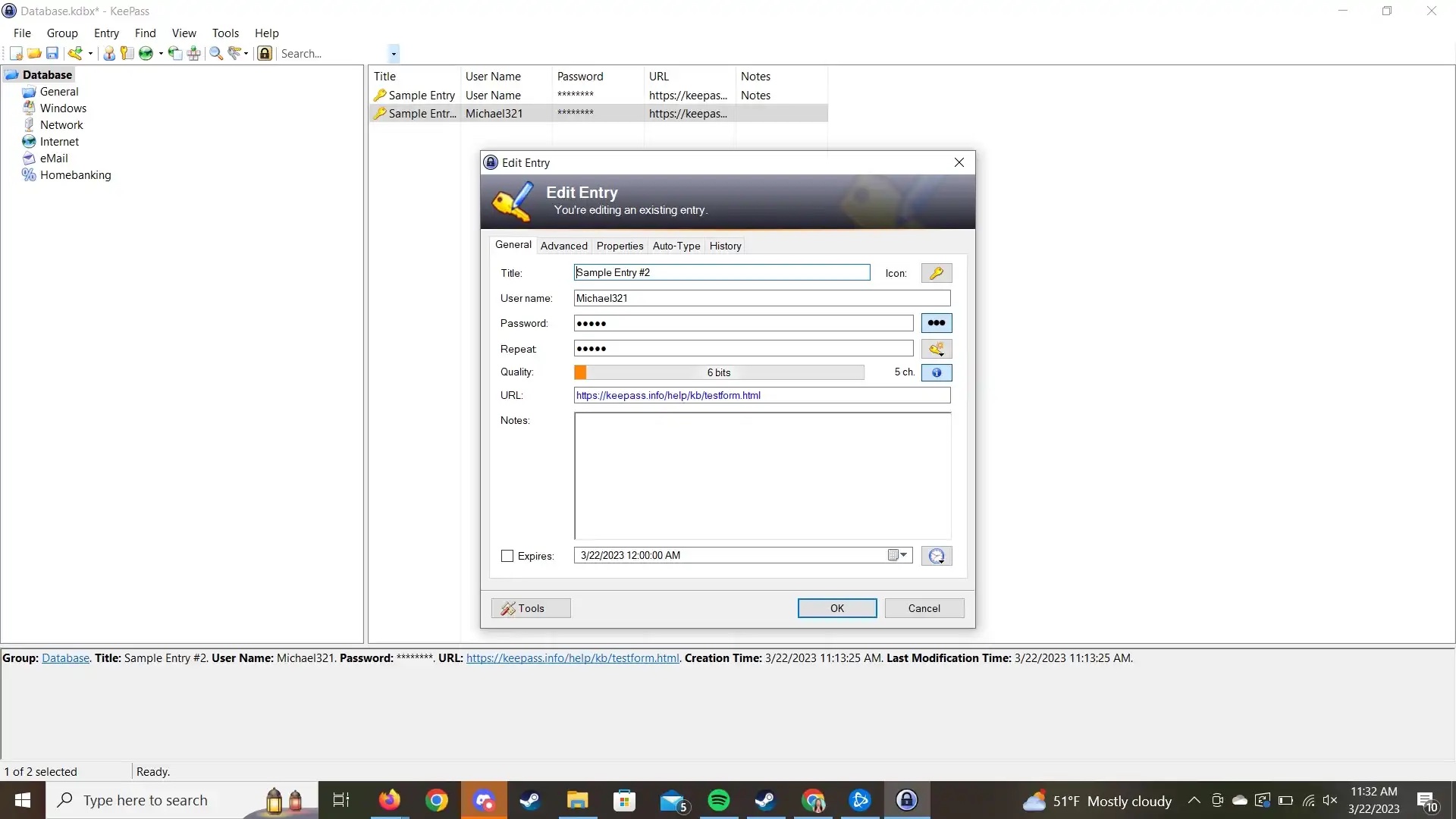
According to Bleeping Computer , a newly discovered memory dump vulnerability in the KeePass application could allow attackers to retrieve master passwords in plain text even if the database is locked or the program is closed. A patch for this critical vulnerability will not be available until early June at the earliest.
A security researcher reported the vulnerability and published a proof-of-concept exploit that allows an attacker to perform a memory scrape to obtain the master password in plaintext, even if the KeePass database is closed, the program is locked, or not even open. When retrieved from memory, the first one or two characters of the password will be missing, but the entire string can then be guessed.
The exploit was written for Windows, but Linux and macOS are also believed to be vulnerable because the issue exists within KeePass and not the operating system. To exploit the password, an attacker would need access to a remote computer (obtained via malware) or directly on the victim's machine.
According to security experts, all KeePass 2.x versions are affected. But KeePass 1.x, KeePassXC, and Strongbox – other password managers compatible with KeePass database files – are not affected.
The fix will be included in KeePass version 2.54, which could be released in early June.
New security flaw puts KeePass at risk as no patch is available yet
There is now an unstable beta version of KeePass with mitigations in place, but a report from Bleeping Computer says the security researcher has been unable to reproduce the password theft from the vulnerability.
However, even after KeePass is upgraded to a fixed version, passwords can still be viewed in the program's memory files. For complete protection, users will need to completely wipe the computer by overwriting existing data, then reinstall a new operating system.
Experts advise that a good antivirus program will minimize the possibility, and users should change their KeePass master password once the official version is available.
Source link


![[Photo] President of the Cuban National Assembly visits President Ho Chi Minh's Mausoleum](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/1/39f1142310fc4dae9e3de4fcc9ac2ed0)



![[Photo] Hanoi morning of October 1: Prolonged flooding, people wade to work](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/1/189be28938e3493fa26b2938efa2059e)
![[Photo] Keep your warehouse safe in all situations](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/1/3eb4eceafe68497989865e7faa4e4d0e)
























































































Comment (0)