The digital transformation process is a breakthrough opportunity for businesses. Along with this process, they face many risks of data intrusion and theft. To adapt to the risks in an ever-changing society, businesses need to ensure network security, contributing to ensuring sustainability against developed platforms.
Thousands of security vulnerabilities discovered
At the workshop "Response and recovery of the system after the disaster" held on November 13 by the CYSEEX Information Security Alliance, Mr. Tran Quang Hung - Deputy Director of the Department of Information Security ( Ministry of Information and Communications ) assessed, " In recent years, the exercise has shifted from passive to real-life exercise. Through the exercise, many vulnerabilities have been discovered, contributing to early warning and early detection for the system to become more and more secure.
In the coming time, the drills will focus on response capabilities and flexible recovery capabilities. From 2024 onwards, there will no longer be system tests, but instead will focus on training staff, which is a key factor in ensuring information security. There will be more in-depth and more realistic tests.
The representative of the Department of Information Security also gave statistics that in 2023, more than 100 drills were organized, with the participation of many ministries and businesses. Up to 1,200 vulnerabilities at high and serious levels were discovered (548 serious vulnerabilities, 366 high-level vulnerabilities). In case these 1,200 vulnerabilities were discovered by hackers first, the risk of data loss and system destruction would be very large.

Mr. Tran Quang Hung - Deputy Director of the Department of Information Security (Ministry of Information and Communications).
Preparing for and recovering from cyber security incidents is essential to ensure the safety and stability of information systems against increasingly sophisticated and dangerous attacks.
A series of recent ransomware attacks have targeted individuals and businesses in Vietnam. Statistics show that in 2023, more than 745,000 devices were infected with malware, resulting in a loss of 716 million USD.
In particular, the ransomware-as-a-service (RaaS) model, which provides malware as a service with rapidly increasing profit sharing, has become a serious threat causing great damage to businesses and the community...

Mr. Nguyen Xuan Hoang, Chairman of CYSEEX Alliance.
Mr. Nguyen Xuan Hoang, Chairman of CYSEEX Alliance, Vice Chairman of the Board of Directors of MISA Joint Stock Company, said that with the motto "the best defense is to proactively attack", in 2024, the alliance successfully organized 9 drills on 18 important information systems of alliance members.
In the past 2 years, we have witnessed a series of cyber attacks, especially ransomware attacks. These attacks not only affect information security but also disrupt business operations, causing great damage to the finances, reputation, and prestige of businesses.
"In the face of these dangers, being prepared and improving the ability to respond and restore the system after a disaster is an urgent task," Mr. Hoang shared.
Every business is a target
Mr. Nguyen Cong Cuong - Director of SOC Center - Viettel Cyber Security Company pointed out that many small businesses are still very self-sufficient when they think they will not be the target of hacker groups.
"Many businesses think that if they are not in the economic sector or are not large-scale, hackers will not pay attention to them. However, any industry or company of any size will eventually become a target of attack.
Attack groups that have not invested enough will target small businesses to attack and infiltrate more easily, while large attack groups with high operating costs will often choose large companies to attack, in order to get more money from businesses," Mr. Nguyen Cong Cuong shared.
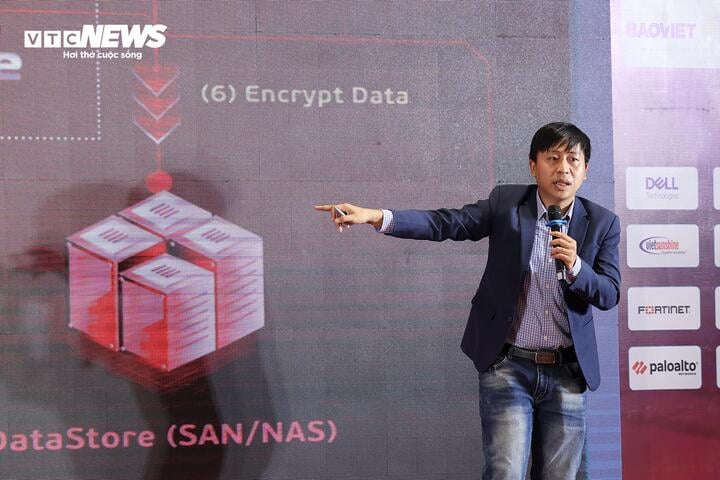
Mr. Nguyen Cong Cuong - Director of SOC Center - Viettel Cyber Security Company.
According to statistics, on average, it takes up to 275 days for an attacker to penetrate a system before it is detected. However, this is only an average number; some systems take several years to be detected.
In fact, large companies in the world have had security vulnerabilities and been hacked. That shows that there is a need to pay attention to managing security vulnerabilities and vulnerabilities.
Mr. Cuong also pointed out 5 common vulnerabilities of many popular businesses such as not performing security vulnerability checks for self-developed or outsourced applications and software; Using third-party operating systems and applications but not regularly updating patches.
High privileged accounts are assigned too many unnecessary rights or the employee has left the company but the account is not revoked; Setting up a server system on the same network, it is easy to access the servers together and finally, the case of many systems conducting online data backup, so when attacked, this data will be immediately encrypted.

Mr. Le Cong Phu, Deputy Director of VNCERT.
At the workshop, Mr. Le Cong Phu, Deputy Director of VNCERT, shared that security technologies have many limitations, because attack techniques and activities change very quickly and are difficult to detect due to encryption.
The first thing that attackers do when they attack the system is to turn off the warning system from the monitoring devices, so we need to proactively handle the situation before the incident occurs, to avoid the attack becoming a disaster, especially in units with large system platforms.
Controlling the entire information system of intruders takes a long time, even weeks or years. The process of "hunting" for threats increases recognition and reduces the time attackers "reside" in the system.
Mr. Phu also emphasized the importance of Threat Hunting in detecting potential security threats.
This is a proactive method of searching for malicious signals without relying on prior warnings, overcoming the limitations of traditional defense technologies.
Threat Hunting reduces the amount of time a threat can persist in a system, while improving the ability to respond quickly to increasingly complex cyber attacks.
Source






![[Photo] Prime Minister Pham Minh Chinh launched a peak emulation campaign to achieve achievements in celebration of the 14th National Party Congress](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/5/8869ec5cdbc740f58fbf2ae73f065076)






























![[Photo] Bustling Mid-Autumn Festival at the Museum of Ethnology](https://vphoto.vietnam.vn/thumb/1200x675/vietnam/resource/IMAGE/2025/10/4/da8d5927734d4ca58e3eced14bc435a3)




















![[VIDEO] Summary of Petrovietnam's 50th Anniversary Ceremony](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/10/4/abe133bdb8114793a16d4fe3e5bd0f12)

![[VIDEO] GENERAL SECRETARY TO LAM AWARDS PETROVIETNAM 8 GOLDEN WORDS: "PIONEER - EXCELLENT - SUSTAINABLE - GLOBAL"](https://vphoto.vietnam.vn/thumb/402x226/vietnam/resource/IMAGE/2025/7/23/c2fdb48863e846cfa9fb8e6ea9cf44e7)

































Comment (0)